In this tutorial I’ll discuss about port security on cisco switch. Port security is a mecanism to secure port switch layer 2 which allows for limitation device that connect to these port based on mac address filters. So that unauthorized device can’t used the port that enables the port security.
When device try to connect to the switch, switch port security will be detect which are authorized mac address or not. If not port security will be doing based what the action configured on port security. The following is action on the port security :
Shutdown :
- Will be disable port or shutdown port and put the port status become err-disable
- Will be send syslog or SNMP when port is disable.
- Violation value will be increased 1 for each unauthorized frames.
Restric :
- Will be discard traffic from unathorized mac address and the interface port will not disabled.
- Send syslog or snmp each received the unauthorized mac address.
- Violation value will be increased 1 for each unauthorized frames.
Protect :
- Is a silent discard, it means the connection from unauthorized mac address will be discard and will not disable port.
- Not to send syslog each unauthorized mac address.
- violation value will not increased.
The following is the topology are used :
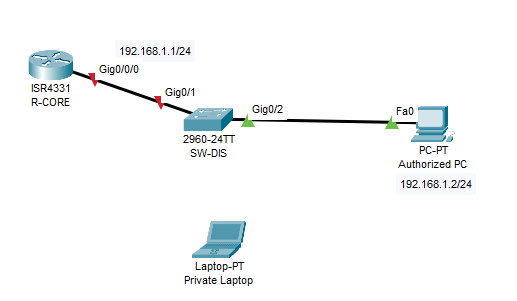
First configure for the normal condition so that PC can connected to the router.
Configure router :
R-CORE(config)#int g0/0/0
R-CORE(config-if)#ip add 192.168.1.1 255.255.255.0
R-CORE(config-if)#no sh
Configure PC :
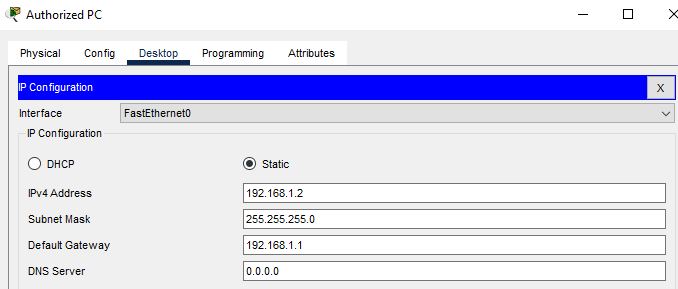
Lest try to ping from PC1 to the router:
C:\>ping 192.168.1.1 Pinging 192.168.1.1 with 32 bytes of data: Reply from 192.168.1.1: bytes=32 time=1ms TTL=255 Reply from 192.168.1.1: bytes=32 time<1ms TTL=255 Reply from 192.168.1.1: bytes=32 time<1ms TTL=255 Reply from 192.168.1.1: bytes=32 time<1ms TTL=255
Connection from PC1 will be successfull.
So, let’s make simulation on this situation. Pretend there are user that bring the personal laptop and trying connect from PC port that connect to the switch (Gig0/1).
We will make the security port if there are unauthorized device try to connect to the gig0/1 port will be discard the traffic and mac address from unauthorized device.
Configured on switch :
SW-DIS(config)#int g0/2 SW-DIS(config-if)#switchport mode access SW-DIS(config-if)#switchport port-security SW-DIS(config-if)#switchport port-security mac-address sticky SW-DIS(config-if)#switchport port-security violation restrict
On the configuration above, we have configured static mode on switchport, enable port security, secure mac address, and violation mode.
Show port security :
SW-DIS#show port-security in SW-DIS#show port-security interface g0/2 Port Security : Enabled Port Status : Secure-up Violation Mode : Restrict Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 0 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0000.0000.0000:0 Security Violation Count : 0
Look at the configure above, there are no device status. Try to ping from PC to the router. after ping show again the command.
SW-DIS#show port-security interface g0/2 Port Security : Enabled Port Status : Secure-up Violation Mode : Restrict Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 1 Last Source Address:Vlan : 0001.9616.1437:1 Security Violation Count : 0
As the shown above, There are sticky mac address or authorized mac address is from the PC Mac address.
Show the running config :
SW-DIS#show run ! interface GigabitEthernet0/2 switchport mode access switchport port-security switchport port-security mac-address sticky switchport port-security violation restrict switchport port-security mac-address sticky 0001.9616.1437 !
As the shown above the sticky mac is the PC mac address so that the PC is an authorized device.
Now try to unplug PC cable and connect Laptop to G0/2 switch port as the following then ping from Laptop to router ip. Dont forget to configure ip for Laptop (192.168.1.3/24)
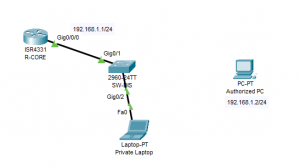
C:\>ping 192.168.1.1 Pinging 192.168.1.1 with 32 bytes of data: Request timed out. Request timed out. Request timed out. Request timed out. Ping statistics for 192.168.1.1: Packets: Sent = 4, Received = 0, Lost = 4 (100% loss), C:\>
The connection is Request Timeout ? Why ? Check to the port security status again .
SW-DIS#show port-security interface g0/2 Port Security : Enabled Port Status : Secure-up Violation Mode : Restrict Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 1 Last Source Address:Vlan : 0009.7C97.A904:1 Security Violation Count : 6 SW-DIS#
Look at the Security Violation count and Last source address. The value is increased and last mac address change to laptop mac address. As we know the laptop is unauthorized device so the security port is detected discard access from laptop mac address and marked by increased the value of violation.
Last try to this article, Plugged back Authorized pc to G0/2 port. and then try ping from PC to the Router ip. is it successfull ? yes of course. then check on port security status again.
SW-DIS#show port-security interface g0/2 Port Security : Enabled Port Status : Secure-up Violation Mode : Restrict Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 1 Last Source Address:Vlan : 0001.9616.1437:1 Security Violation Count : 0
Look at the violation count and last mac address is back to zero and mac address of authorized PC so that the PC can be ping to the router ip.
You can try more autside this article for port security. Happy learning.