Hello everyone, in this tutorial I’ll discuss about how to configure loadsharing connection with DualLink Internet use PBR and IP SLA on Cisco. For the example bellow I have two Internet link for 1st link on ISP1 and 2nd link on ISP2. Then I’ll Divide the connection for the http/s, DNS through ISP1 and other connection through ISP2.
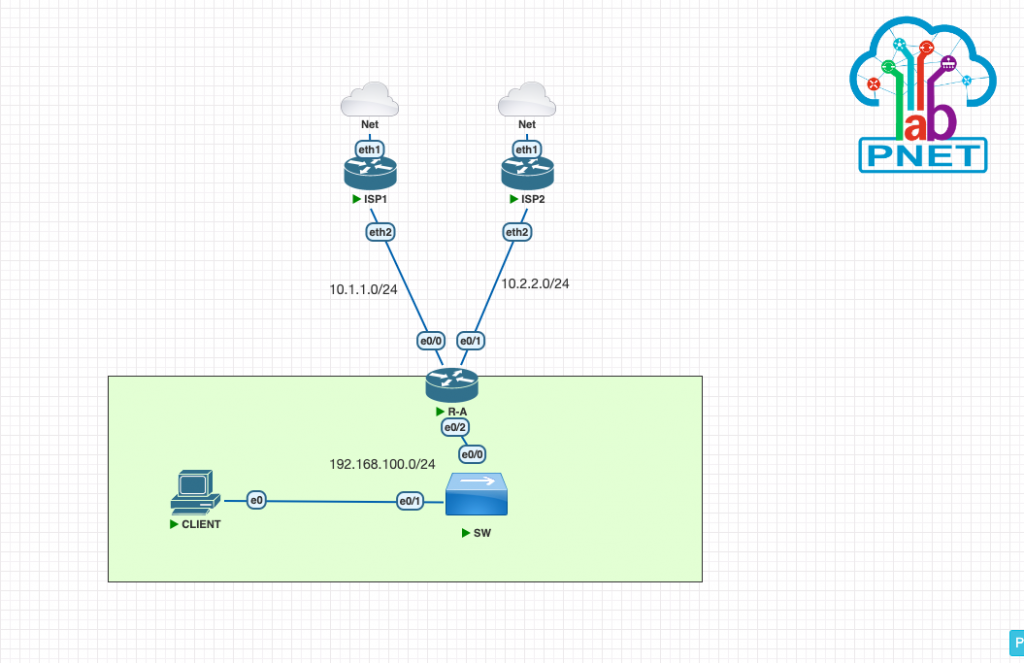
Let say we already configure on ISP link. Then configure ip address on R-A
R-A(config-if)#ip add 10.1.1.2 255.255.255.0 R-A(config-if)#description ISP1 R-A(config-if)#exit R-A(config)#int e0/1 R-A(config-if)#ip add 10.2.2.2 255.255.255.0 R-A(config-if)#des ISP2 R-A(config-if)#exit R-A(config)#
Verification connection to ISP1 (10.1.1.1) and ISP2 (10.2.2.1)
R-A#ping 10.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/8 ms R-A#ping 10.2.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.2.2.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/8 ms R-A#
Configure ip address for LAN connection :
R-A(config)#int e0/2 R-A(config-if)#no shut *Oct 20 09:13:22.155: %LINK-3-UPDOWN: Interface Ethernet0/2, changed state to up *Oct 20 09:13:23.159: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/2, changed state to up R-A(config-if)#ip add 192.168.100.1 255.255.255.0 R-A(config-if)#des LAN R-A(config-if)#
Configure IP NAT outside on both internet link :
R-A(config)#int e0/0 R-A(config-if)#ip nat outside R-A(config-if)#exit R-A(config)#int e0/1 R-A(config-if)#ip nat outside R-A(config-if)#exit
Configure IP NAT inside on LAN link and configure for Policy route-map
R-A(config)#int e0/2 R-A(config-if)#ip nat inside R-A(config-if)#ip policy route-map PBR R-A(config-if)#exit
Configure IP SLA for monitoring each Internet links. IP SLA 1 to monitor ISP1 link and IP SLA 2 to monitor ISP2 link. For the configuration of ip sla we need to set timeout for 500ms and ip sla will send icmp echo every 1 second.
R-A(config)#ip sla 1 R-A(config-ip-sla)#icmp-echo 10.1.1.1 R-A(config-ip-sla-echo)#timeout 500 R-A(config-ip-sla-echo)#frequency 1 R-A(config-ip-sla-echo)#exit R-A(config)#ip sla 2 R-A(config-ip-sla)#icmp-echo 10.2.2.1 R-A(config-ip-sla-echo)#timeout 500 R-A(config-ip-sla-echo)#frequency 1 R-A(config-ip-sla-echo)#exit
Start the configuration for IP SLA :
R-A(config)#ip sla schedule 1 start-time now life forever R-A(config)#ip sla schedule 2 start-time now life forever
Configuration track for ip sla 1 and 2. Set if track didn’t receive icmp echo within 5 second, track 1 or 2 will considered as down.
R-A(config)#track 1 ip sla 1 reachability R-A(config-track)#delay up 5 down 5 R-A(config-track)#exit R-A(config)#track 2 ip sla 2 reachability R-A(config-track)#delay up 5 down 5 R-A(config-track)#exit R-A(config)#
Verification track status
R-A#show track Track 1 IP SLA 1 reachability Reachability is Up 1 change, last change 00:00:57 Delay up 5 secs, down 5 secs Latest operation return code: OK Latest RTT (millisecs) 1 Track 2 IP SLA 2 reachability Reachability is Up 1 change, last change 00:00:44 Delay up 5 secs, down 5 secs Latest operation return code: OK Latest RTT (millisecs) 4 R-A#
Configuration default route to ISP1 and ISP2 with each track
R-A(config)#ip route 0.0.0.0 0.0.0.0 10.1.1.1 track 1 R-A(config)#ip route 0.0.0.0 0.0.0.0 10.2.2.1 track 2
Verification ip route
R-A#show ip route ................ Gateway of last resort is 10.2.2.1 to network 0.0.0.0 S* 0.0.0.0/0 [1/0] via 10.2.2.1 [1/0] via 10.1.1.1 10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks C 10.1.1.0/24 is directly connected, Ethernet0/0
After configuration ip sla and route is successfull, then I’ll continue to configure Ip Access List.
Configure Standard Access List for LAN Network
R-A(config)#ip access-list standard LAN R-A(config-std-nacl)#permit 192.168.100.0 0.0.0.255 R-A(config-std-nacl)#exit
Then Configure Extended Access list for Divided the internet connection. First configure Access list for http/s and domain connection with POL-1 and other on POL-2
R-A(config)#ip access-list extended POL-1 R-A(config-ext-nacl)#permit tcp 192.168.100.0 0.0.0.255 any eq www R-A(config-ext-nacl)#permit tcp 192.168.100.0 0.0.0.255 any eq 443 R-A(config-ext-nacl)#permit tcp 192.168.100.0 0.0.0.255 any eq domain R-A(config-ext-nacl)#permit udp 192.168.100.0 0.0.0.255 any eq domain R-A(config-ext-nacl)#exitR-A(config)#ip access-list extended POL-2 R-A(config-ext-nacl)#permit ip any any R-A(config-ext-nacl)#exit R-A(config)#
Afterthat configure the Route-map for mapping connection based on IP Access list and ip sla for monitoring.
R-A(config)#route-map PBR permit 10 R-A(config-route-map)#match ip address POL-1 R-A(config-route-map)#set ip next-hop verify-availability 10.1.1.1 1 track 1 R-A(config-route-map)#exit R-A(config)#route-map PBR 20 R-A(config-route-map)#match ip address POL-2 R-A(config-route-map)#set ip next-hop verify-availability 10.2.2.1 2 track 2 R-A(config-route-map)#exit R-A(config)#
Verification Route-map Connection
R-A#show route-map route-map PBR, permit, sequence 10 Match clauses: ip address (access-lists): POL-1 Set clauses: ip next-hop verify-availability 10.1.1.1 1 track 1 [up] Policy routing matches: 0 packets, 0 bytes route-map PBR, permit, sequence 20 Match clauses: ip address (access-lists): POL-2 Set clauses: ip next-hop verify-availability 10.2.2.1 2 track 2 [up] Policy routing matches: 0 packets, 0 bytes R-A#
Next I’ll create 2 route-maps for Controlling Routing Table and PBR Choise. These route-map will used for NAT Connection.
R-A(config)#route-map ISP1 permit 10 R-A(config-route-map)#match ip address LAN R-A(config-route-map)#match interface e0/0 R-A(config-route-map)#exit R-A(config)#route-map ISP2 permit 10 R-A(config-route-map)#match ip address LAN R-A(config-route-map)#match interface e0/1 R-A(config-route-map)#exit R-A(config)#
Verification Route-Map
R-A#show route-map route-map PBR, permit, sequence 10 Match clauses: ip address (access-lists): POL-1 Set clauses: ip next-hop verify-availability 10.1.1.1 1 track 1 [up] Policy routing matches: 0 packets, 0 bytes route-map PBR, permit, sequence 20 Match clauses: ip address (access-lists): POL-2 Set clauses: ip next-hop verify-availability 10.2.2.1 2 track 2 [up] Policy routing matches: 0 packets, 0 bytes route-map ISP2, permit, sequence 10 Match clauses: ip address (access-lists): LAN interface Ethernet0/1 Set clauses: Policy routing matches: 0 packets, 0 bytes route-map ISP1, permit, sequence 10 Match clauses: ip address (access-lists): LAN interface Ethernet0/0 Set clauses: Policy routing matches: 0 packets, 0 bytes R-A#
Configuration NAT with source route-map that we have create before.
R-A(config)#ip nat inside source route-map ISP1 interface e0/0 overload R-A(config)#ip nat inside source route-map ISP2 interface e0/1 overload
Then activate debug ip nat to testing the connection
R-A#debug ip nat IP NAT debugging is on R-A#
I have test ping connection to 8.8.8.8 and connection will access from ISP2 network as the shown bellow
R-A# *Oct 21 12:09:04.195: NAT*: s=192.168.100.2->10.2.2.2, d=8.8.8.8 [5977] *Oct 21 12:09:04.235: NAT*: s=8.8.8.8, d=10.2.2.2->192.168.100.2 [19855] *Oct 21 12:09:05.199: NAT*: s=192.168.100.2->10.2.2.2, d=8.8.8.8 [5978] R-A# *Oct 21 12:09:05.227: NAT*: s=8.8.8.8, d=10.2.2.2->192.168.100.2 [19856] *Oct 21 12:09:06.191: NAT*: s=192.168.100.2->10.2.2.2, d=8.8.8.8 [5979] *Oct 21 12:09:06.227: NAT*: s=8.8.8.8, d=10.2.2.2->192.168.100.2 [19857] R-A# R-A#show ip nat trans R-A#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 10.2.2.2:1 192.168.100.2:1 8.8.8.8:1 8.8.8.8:1 R-A#
Then I Will test Domain & http/s connection from the client. As the shown bellow we can see the connection will through ISP1 link as the define at the IP Access list.
R-A# *Oct 21 10:44:48.955: NAT: s=192.168.100.2->10.1.1.2, d=8.8.8.8 [160] *Oct 21 10:44:49.543: NAT: s=8.8.8.8, d=10.1.1.2->192.168.100.2 [166] *Oct 21 10:44:49.555: NAT: s=192.168.100.2->10.1.1.2, d=8.8.8.8 [161] *Oct 21 10:44:49.575: NAT: s=8.8.8.8, d=10.1.1.2->192.168.100.2 [167] *Oct 21 10:44:49.583: NAT: s=192.168.100.2->10.1.1.2, d=8.8.8.8 [162] *Oct 21 10:44:49.599: NAT: s=8.8.8.8, d=10.1.1.2->192.168.100.2 [168] R-A#show ip nat trans Pro Inside global Inside local Outside local Outside global udp 10.2.2.2:137 192.168.100.2:137 192.168.100.255:137 192.168.100.255:137 udp 10.1.1.2:61323 192.168.100.2:61323 8.8.8.8:53 8.8.8.8:53 udp 10.1.1.2:61324 192.168.100.2:61324 8.8.8.8:53 8.8.8.8:53 udp 10.1.1.2:61325 192.168.100.2:61325 8.8.8.8:53 8.8.8.8:53 R-A# *Oct 21 10:47:29.011: NAT*: s=192.168.100.2->10.1.1.2, d=142.250.4.94 [5557] *Oct 21 10:47:29.099: NAT*: s=192.168.100.2->10.1.1.2, d=34.117.237.239 [5558] *Oct 21 10:47:29.099: NAT*: s=192.168.100.2->10.1.1.2, d=142.250.4.94 [5559] *Oct 21 10:47:29.435: NAT*: s=192.168.100.2->10.1.1.2, d=35.244.181.201 [5562] *Oct 21 10:47:29.435: NAT*: s=192.168.100.2->10.1.1.2, d=152.195.38.76 [5563] R-A#show ip nat translations Pro Inside global Inside local Outside local Outside global udp 10.2.2.2:137 192.168.100.2:137 192.168.100.255:137 192.168.100.255:137 tcp 10.1.1.2:49194 192.168.100.2:49194 35.244.181.201:443 35.244.181.201:443 tcp 10.1.1.2:49195 192.168.100.2:49195 36.89.220.121:80 36.89.220.121:80 tcp 10.1.1.2:49196 192.168.100.2:49196 36.89.220.121:80 36.89.220.121:80 tcp 10.1.1.2:49197 192.168.100.2:49197 216.239.38.120:443 216.239.38.120:443
The Result for Those configuration, We can divided the connection to two links or more with PBR and also monitoring connection with IP SLA.