Hello everywhere, in this tutorial I’ll Discuss about how to configure the basic fortigate firewall
Here’s the topology are used :
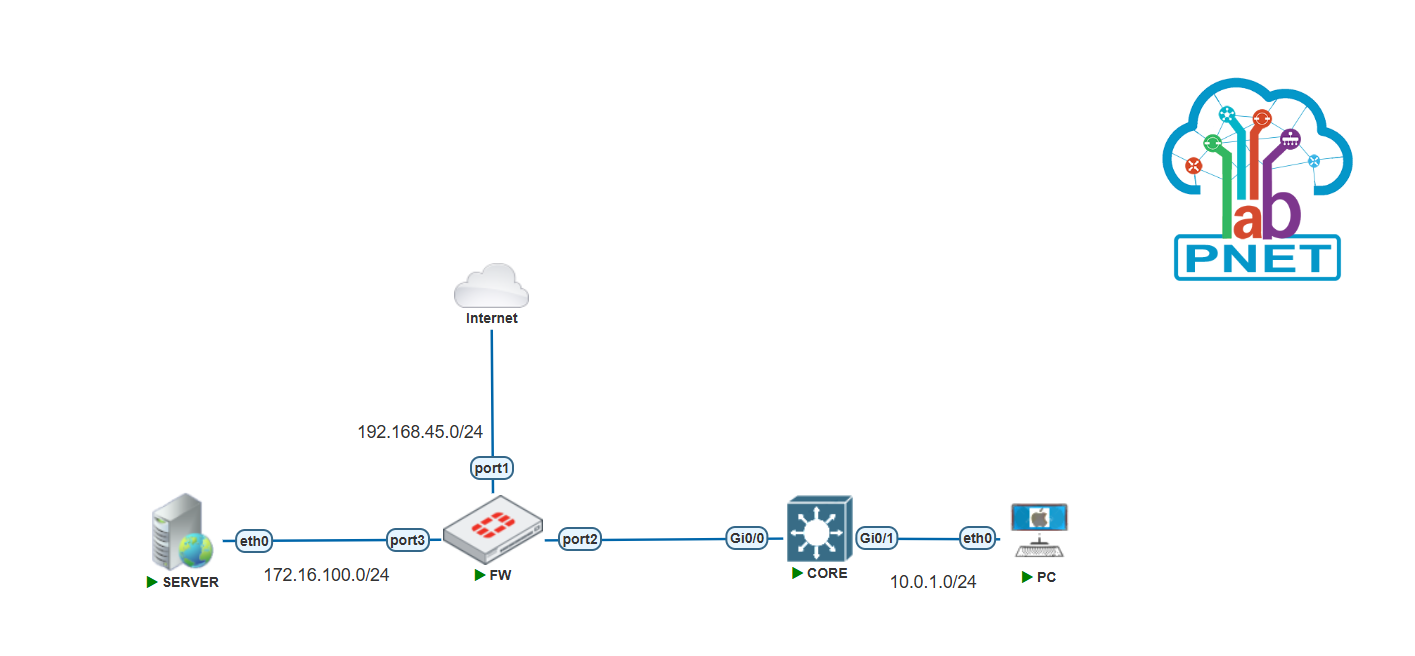
First step access to Fortigate, the default login is admin and password is blank. After you enter the password, it’s immediately forced to change a new password.
Configure Hostname :
FortiGate-VM64-KVM # config system global FortiGate-VM64-KVM (global) # set hostname MyFW FortiGate-VM64-KVM (global) # end MyFW #
To configure and show the interface/port configuration, enter the config system interface command.
Show the port setting with show command
MyFW # config system interface MyFW (interface) # show config system interface edit "port1" set vdom "root" set mode dhcp set allowaccess ping https ssh http fgfm set type physical set snmp-index 1 next edit "port2" set vdom "root" set type physical set snmp-index 2 next edit "port3" set vdom "root" set type physical set snmp-index 3 next
To configure ip address on port, use edit command on port that will config. To configure static ip, use SET command with mode static first and then configure the ip address on interface port. Don’t forget to set allowed access to firewall so you can access from GUI or CLI remote.
MyFW (interface) # edit port1 MyFW (port1) # set mode static MyFW (port1) # set ip 192.168.45.136/24 MyFW (port1) # set allowaccess ping https ssh http fgfm MyFW (port1) # end
Show configuration interface with get command
MyFW (interface) # get port1 name : port1 vdom : root vrf : 0 cli-conn-status : 0 fortilink : disable mode : static dhcp-relay-interface-select-method: auto dhcp-relay-service : disable ip : 192.168.45.136 255.255.255.0 allowaccess : ping https ssh http fgfm fail-detect : disable pptp-client : disable
Configure gateway with config router static command
MyFW # config router static MyFW (static) # edit 1 MyFW (1) # set gateway 192.168.45.2 MyFW (1) # end MyFW #
Configure DNS
MyFW # config system dns MyFW (dns) # set primary 8.8.8.8 MyFW (dns) # set secondary 8.8.4.4 MyFW (dns) # end MyFW #
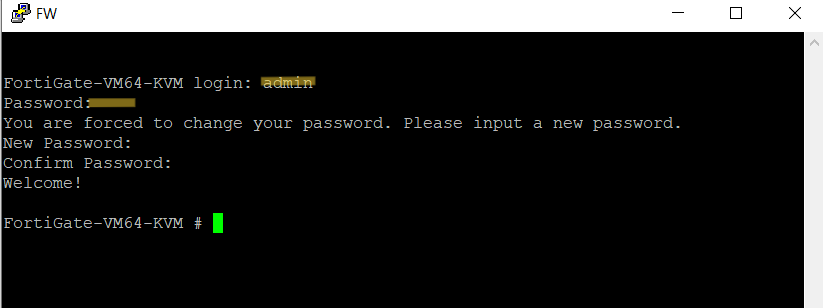
Now access via GUI. Login with username & password that same with cli login.
Login access successfull
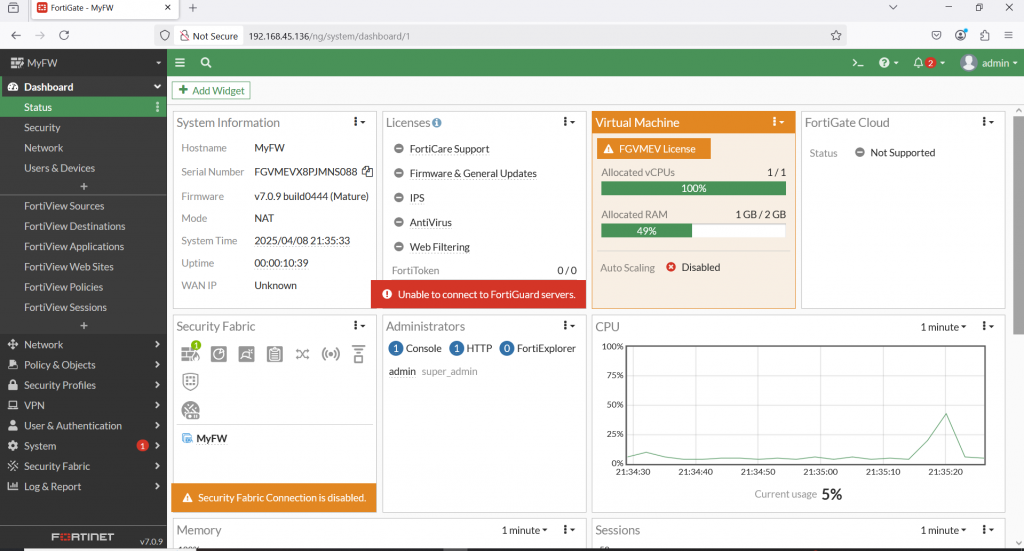
Now edit and check the interface port1 on GUI access. Select Network à Interfaces TAB à Select port1 and then click Edit button.
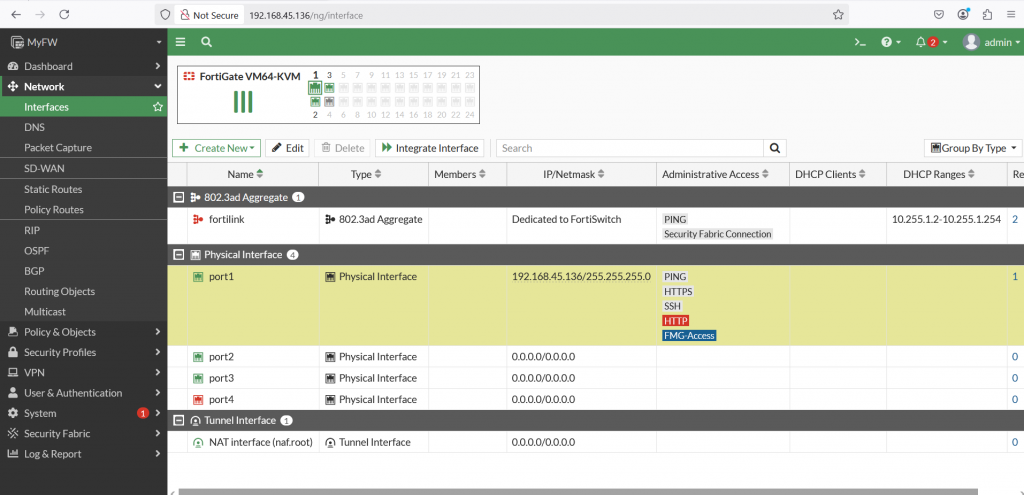
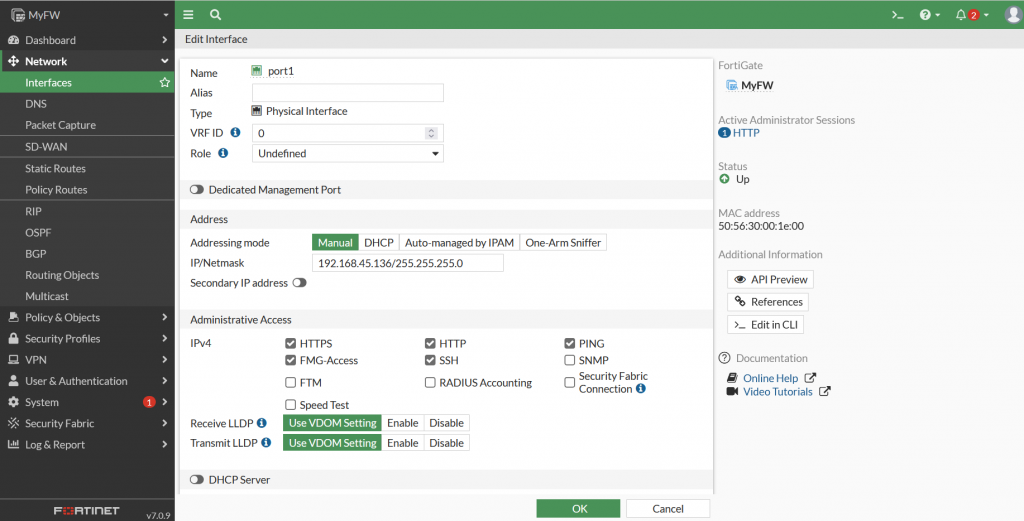
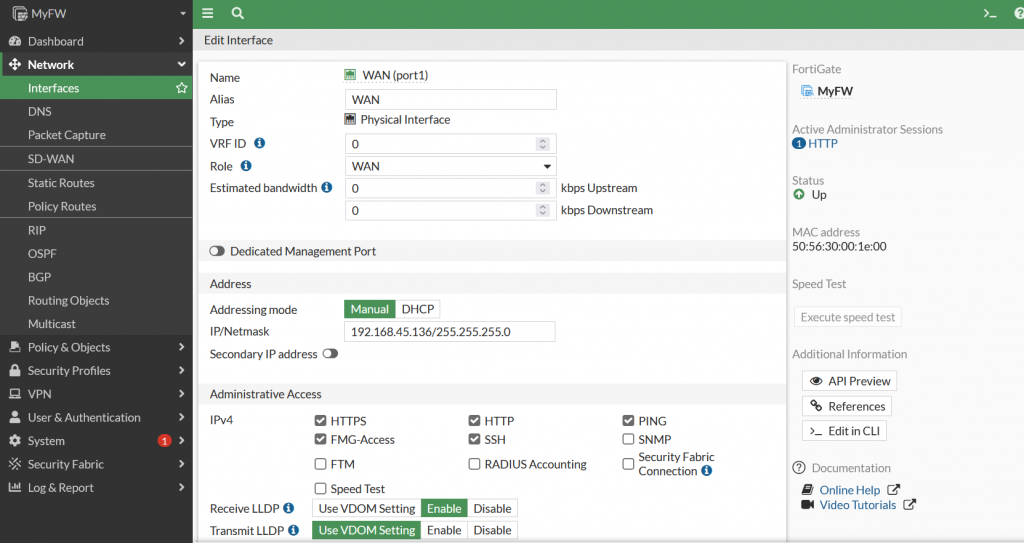
Edit Alias with WAN and Role WAN. Then select OK. You can also configure the Administrative Access to limit IPv4 Access method through WAN (port1) .
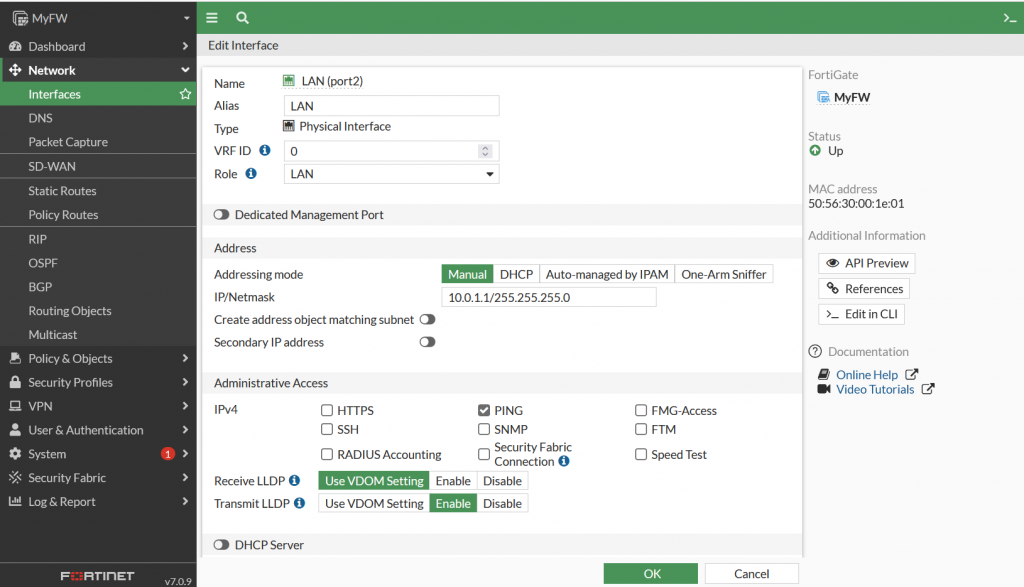
Configure Port 2 for the LAN Access. Select Port2 and click Edit Button. Set Alias with LAN, Role LAN. Configure Address Mode with Manual then enter IP/Netmask. Enable Administrative Access to PING.
Configure Port3 for Server access. Use Role DMZ.
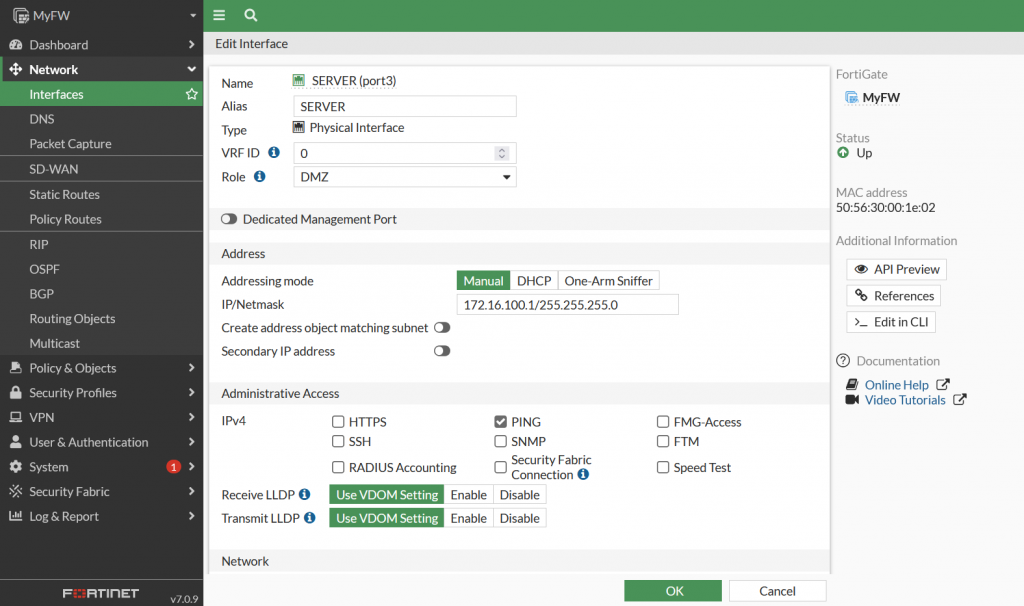
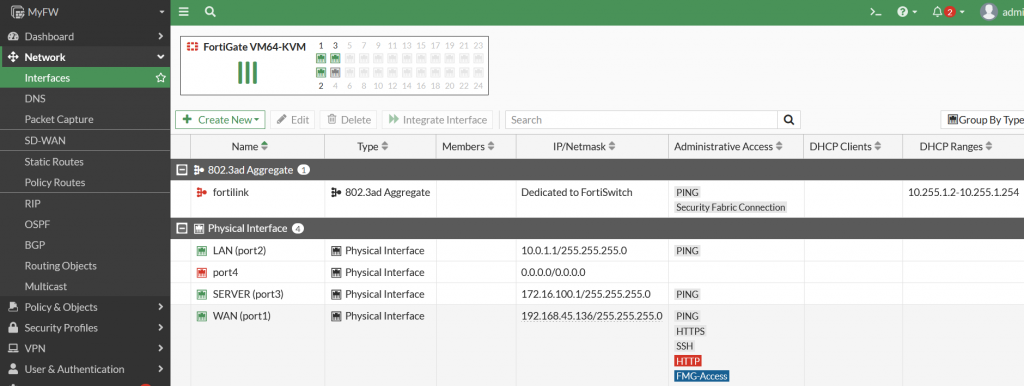
Configure IP Address on PC and test ping to Gateway (interface port2 fortigate)
PC> ip 10.0.1.2/24 10.0.1.1 Checking for duplicate address... PC1 : 10.0.1.2 255.255.255.0 gateway 10.0.1.1
PC> ping 10.0.1.1 84 bytes from 10.0.1.1 icmp_seq=1 ttl=255 time=2.167 ms 84 bytes from 10.0.1.1 icmp_seq=2 ttl=255 time=2.570 ms 84 bytes from 10.0.1.1 icmp_seq=3 ttl=255 time=2.733 ms
Then configure IP Address on SERVER and test ping to Gateway also (interface port3 fortigate)
SERVER> ip 172.16.100.2/24 172.16.100.1 Checking for duplicate address... PC1 : 172.16.100.2 255.255.255.0 gateway 172.16.100.1
SERVER> ping 172.16.100.1 84 bytes from 172.16.100.1 icmp_seq=1 ttl=255 time=0.397 ms 84 bytes from 172.16.100.1 icmp_seq=2 ttl=255 time=0.452 ms 84 bytes from 172.16.100.1 icmp_seq=3 ttl=255 time=0.425 ms
Now to test connection Fortigate from GUI, click CLI console on the Top Right
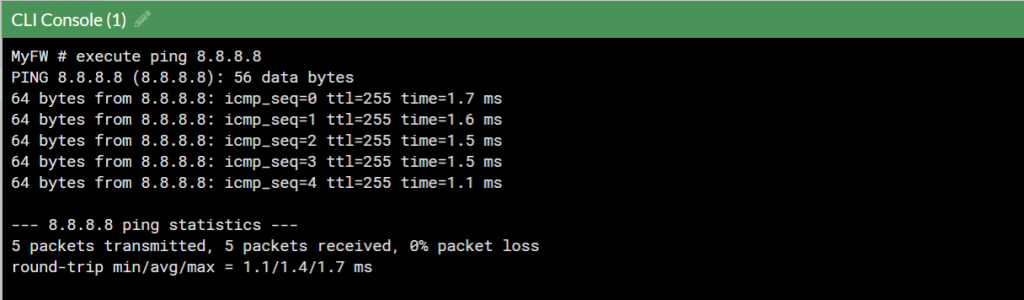
Use Execute ping command to ping test. The fortigate is successful to access to outside network.
After that, try to test ping from the PC to SERVER and 8.8.8.8. As the shown bellow, PC is timeout to connect to SERVER & outside network.
PC> ping 172.16.100.2 172.16.100.2 icmp_seq=1 timeout 172.16.100.2 icmp_seq=2 timeout 172.16.100.2 icmp_seq=3 timeout
PC> ping 8.8.8.8 8.8.8.8 icmp_seq=1 timeout 8.8.8.8 icmp_seq=2 timeout 8.8.8.8 icmp_seq=3 timeout
And SERVER also can’t connect to the PC & outside network.
SERVER> ping 10.0.1.2 10.0.1.2 icmp_seq=1 timeout 10.0.1.2 icmp_seq=2 timeout 10.0.1.2 icmp_seq=3 timeout
SERVER> ping 8.8.8.8 8.8.8.8 icmp_seq=1 timeout 8.8.8.8 icmp_seq=2 timeout 8.8.8.8 icmp_seq=3 timeout
These occur because we do not configure the Firewall Policy yet. We want to discuss about firewall policy in the next article.